�
Protection of a mobile application is one of the most important stages of its development. Without taking proper measures, a cracked copy of it can quickly appear on the Web, in which, for example, advertising and verification via social services will be disabled. But the main danger is that the pirate will be able to decompile the application in order to learn it from the inside and recreate the same. There are a number of measures to protect an app. What should be used depends on the specifics of the project.
We bring to your attention the 9 tricks that App developers use to protect information.
1. Prevent decompilation
Obtaining the source code of an unprotected application is not a problem for an experienced developer. To do this, simply convert to jar dex files, and then extract the source-code which is easy to read. This can be prevented with the help of special tools: JAD, JD-GUI, and dex2jar. But it should be understood that the application cannot be fully protected from reverse engineering. It is only possible to complicate the task of the pirates so that it was not profitable for him to engage in hacking.
Obfuscation of code to prevent it from being studied.
App developers use tools tool to minimize the chance of hacking their apps. Such tools perform a lot of functions but the main thing is that they are able to obfuscate the code. This would confuse the hacker so that he would have a hard time figuring out what was happening. The principle of operation of this tool is as follows: search for unused blocks of code with their subsequent removal; analysis of byte-code methods with its subsequent optimization; Renaming the names of variables, classes, methods, etc. The first two procedures optimize the code, and the third makes it difficult to read.
Writing some C/C++ program modules
To increase data protection, which must be stored on the client device, App developers use the
NDK. With its help, it is possible to take out a part of the code in .so-files. It, in turn, is written in C or C ++. The results of decompiling/disassembling such code are difficult to read, which minimizes the likelihood of their unauthorized use in other projects.
2. Transfer part of the application to the server
One of the most effective ways to protect an application is to transfer a critical part of a program to a server — for example, unique algorithms. In this case, important data will be saved from hacking due to the fact that penetrating a properly configured server is an extremely difficult task.
3. Encryption
If the application transmits data to the server, then SSL should be used. However, its use must be approached responsibly. About 40% of all applications using SSL are vulnerable to a man-in-the-middle attack.
4. Storage of important user data in processed form
It is not a good idea to store important user information plainly. It is better to process it using a special algorithm.
5. Work with credentials
In order for the application to be protected, you need to refuse to store the password on the user's device (for a permanent login, it is better to use the Credential object). It is also important in the application to minimize the number of credential requests. You should contact top mobile app development companies to hire App developers for the development of your mobile app.
6. Responsible use of API keys
Using API keys is a convenient way to authenticate a particular user's connection. But they cannot be stored in places that have free access, because otherwise, the hacker will be able to get the secret code by decompiling the APK file.
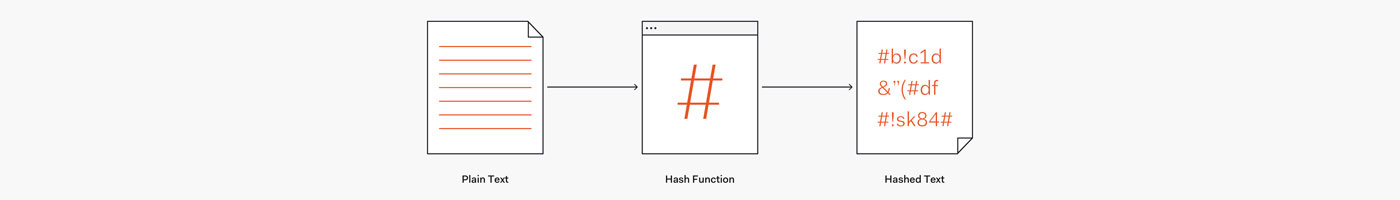
7. Use reliable hash functions
Another important nuance on which application security depends is the use of a reliable
hash function. Currently, it is SHA-2. Others, such as MD2, MD5, and SHA1, have known vulnerabilities due to which processed confidential information (such as passwords) may be compromised. It is important here that the hash function is not only stable but also quite slow - this complicates the search. These include, in particular, scrypt, bcrypt, and PBKDF2.
8. Preventing the use of invalid arguments
In a secure application, there is no ability to execute arbitrary commands. To do this, you must create whitelist valid, and allow users to select only from those present in it. Otherwise, the attacker will be able to pass an argument to the function that was not intended by the developer, which, for example, will bypass access restrictions.
9. The ban on the installation of data on an external drive
When the user connects the device to the computer as a USB drive, full access to the files on the memory card opens. In addition, after the application is deleted, the information recorded on the MicroSD may remain on it. This, in turn, can lead to the compromise of confidential data. We use SQLite to eliminate the damage from storing critical information on external drives. Despite the fact that the above measures do not guarantee complete security, they minimize the likelihood of hacking. Therefore, be sure to include the security requirements for the application in the technical task. You should contact top mobile app development companies to hire App developers.